Introduction
In an earlier lesson we introduced the concept of security within local area networks. There is often a lot of sensitive information stored in a local area network. If unauthorised people where to get this information, this would lead to some unwanted consequences. Examples of such sensitive information are personal information about the employees that are not meant for the public, information about the firm's wage-system where the employees are not supposed to be able to change their own wage. Another problem with local area network is industrial espionage, both from local and foreign people.
We often divide the security risk into two groups; leaks within the business, and leaks from the outside. The biggest risk is from those inside the firm. They often have the easiest access to information. Most problems with leaks are founded in local people. There are several ways to reduce (almost eliminate) such insider leaks. We will discuss some of those later in this lesson.
The other group, those outside the firm, is those often referred to as "hackers". Different computer communication networks are growing increasingly tighter together. This also increases the risk of unauthorised access to the local server. The Internet makes the work for these persons easier. Many of the persons that actively do their best to access information on different systems, have a lot of competence, and are very hard to lock out. The only certain method is not to link your network to other networks. Often the advantages to connecting to other networks are so high that firms with a low security risk takes the chance, and instead does their best to make the intrusion as difficult as possible. We will take a look at some ways later in this lesson.
Administration of a local area network is a very important task, and it is here the possibilities to limit the risks for information leaks lye. Administration consists of several different tasks, and security consists of several subtasks. Taking backups periodically is one of the more important subtasks in security. There are often problems with lost data, and it is important to have thorough and well-planned routines for safety backups. How often backups should be done, and how long a backup should be saved, varies with the size of the firm. We will discuss this in a later lesson. Another important subtask is the security for the printer environment. We will discuss this also in a later lesson.
LAN security
A society of users…
Often the local area network environment is compared with a society of
users. By society I mean a hierarchically society. The thought behind
this structure of society is that some of the users have to have rights
the other users don't have. We could say that they have special powers.
Normal members of the society, or the citizens, in this society are
called users. The users are often organised in groups to have
some sort of order, and to make it easier to keep a set of rules. To best keep
the "national security" it is important to give a few people the right
to spy on the network to discover possible "leak-areas". If such a "spy"
discovers something suspicious, he should have the possibility to examine his
suspicion more closely. If it proves correct, he also should have the
possibility to do something about it. If we look at a network this way, we can
see that it is a hierarchically society with the system administrator as
the supreme leader. The system administrator has the possibility to read
everybody's files, and to "disconnect" someone from the "society".
This way a system administrator will have much more power than any politic
leader today (the politic leaders are not (should not be) allowed to enter
anybody's private life and to dismiss anybody from the society). It is therefore
important to have a system administrator that are trusted, and that do not use
such measures unless they are absolutely necessary.

When I say that the network society is hierarchically, I do not mean a hierarchy with only two levels. In big local area networks there are often several levels. On the top there are the person responsible for the network, in large firms often called IT-manager. This manager often has a government, also called a network group. The IT-manager has access to all information in the network. A possible level beneath the manger could be the system-operators. These only have access to information stored in their part of the network. Beneath these there might be users with special rights. These might be group-administrators and printer administrators.
A group administrator has the rights to add or remove users from his group, and to grant or remove rights to read, write and delete files and folders. A printer administrator has responsibility for printers and printer queues. Print queues are known to freeze occasionally, on those occasions this person might remove the offending print-process, and let the waiting print-processes continue. The printer-administrator is also allowed to grant and remove rights or priorities to users or processes.
At the bottom of the system are the users who have to live with those who are placed above them. Figure 1 shows us an example of such a network hierarchy.
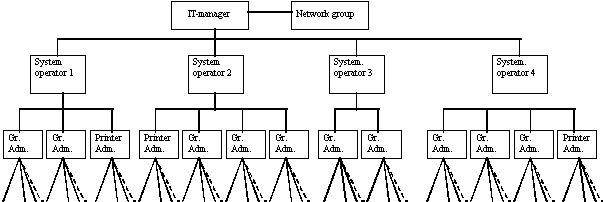
Figure 1 - Network hierarchy
This way of organising the network is practical in large network-systems. It makes the job easier for those who are responsible for the network administration. It also brings the network closer to the users since the system-operators and group-administrators work in their department and group.
The user environment.
I said that the normal users are located at the bottom of the network society. When defining the user environment, it is important to recognise everybody in the network as a user, also the IT-Manager and system-operators. The user environment is a definition of what all the users are allowed to access. In other words the user environment is a definition of all the users rights to:
- Printers
- files
- workstations
- other equipment
- What time of day the users has access rights.
Securing data
We can divide security in two groups; physical security and computer access security. Physical security is securing the computer equipment with locks and other physical equipment. Computer access security is the most demanding one. Intruders in computer systems do not care for doors. They use the phone-lines, cables and network-adapters as entry ports. Computer access security is an attempt to prevent such intrusion, or at least make it as difficult as possible.
The level of security, both physical and computer access depends on the consequences of a possible intrusion. Too much security makes a big and slow system. The users quickly grows tired of having to pass through several "security gates" each time they are supposed to use the network. Little security opens for the risk of loosing data, which might lead to grave consequences.
Physical security
 Physical security means to secure the
computer equipment with locks, alarms and detectors to prevent unauthorised
access to servers, workstations or any other equipment. Especially important is
the room where the server is placed. This should be a separate room. The door to
this room should have a good lock. The consequences are great if anybody should
sabotage or steal any equipment from this room. Turning off the server can often
cause serious damage to the network. This is also a reason to why this room
should be properly secured. It would be just as bad if a well meaning employee
should turn off the computer to conserve energy.
Physical security means to secure the
computer equipment with locks, alarms and detectors to prevent unauthorised
access to servers, workstations or any other equipment. Especially important is
the room where the server is placed. This should be a separate room. The door to
this room should have a good lock. The consequences are great if anybody should
sabotage or steal any equipment from this room. Turning off the server can often
cause serious damage to the network. This is also a reason to why this room
should be properly secured. It would be just as bad if a well meaning employee
should turn off the computer to conserve energy.
Computer Access security
The most difficult task concerning security is keeping unauthorised people outside the network. We might as well say that it is an impossible task. There are many that have so much knowledge about breaking into networks, that if you gave them enough time, they will succeed.
There fore we can conclude that the security is, at least, a hindrance that makes it possible to detect and fend off an intrusion before any damage is done, or to make the intrusion so difficult and time consuming that it doesn't pay off.
Passwords
Password protection is the most used computer access security method. Password is used to verify a user as the person he claims to be when he logs on the network It is important to make rules for the user to guide them in their choice of password. The rules could be:
- Forced periodically password change (for example at least each month)
- No reuse of old passwords.
- Minimum number of signs
- Use of special letters (for example @£$%*~)
- Mixing of small and capital letters.
Most network operating systems gives the system administrator the possibility to limit the choices of passwords to make the users follow the rules.
It is very important to choose imaginative passwords. The most used American passwords are "beer", "fuck" and "sex". A student at a university in Scotland discovered 60% of all the passwords at that university during one weekend. This is because most people use normal words as their passwords. This makes it possible to run a dictionary against the password verification. A good rule is to never choose normal words, but a more or less random collection of letters, for example "IPAIFTS". These seemingly random letters can be an abbreviation for sentences that mean something (Imaginative Passwords Are Important For The Security) that makes them easier to remember. Passwords like this are as good as impossible to discover. It gets even better if we choose passwords that utilises special letters or numbers; Lot2 Gave 5 Hundred Thousand = L2G5HT.
Reactions against users who do not enter the right password can be different. Three reactions could be:
- Timeout values - The user has to wait a given time before he can start again with a new password. This delays the intruder so much that they hopefully won't have the patience to try enough passwords to discover the right one. Such a timeout can be started after a given number of tries.
- Deactivating a user - If a user enters the incorrect password he cannot enter the network before he has talked to the system operator and got the account activated again. This can also be activated after a number of tries.
- Fake logon is a reaction for network with large consequences following an intrusion. This allows a user to log onto the network even though the password is wrong. The account only gives him access to a very limited area, and the system operator is notified about the intruder. This method opens for discovery and punishment of intruders.
As an example, Novell NetWare has the following security measures concerning passwords:
- Demand a password change at regular intervals. If this interval is broken, the account is closed (possibly after a number of warnings).
- Demand a minimum password length
- Demand new passwords each time it is changed - Novell "remembers" old passwords quite long, so it is not possible to swap between a few passwords.
Figure 2 shows us the password rules for a user, james, in a Novell 4.1 -network.
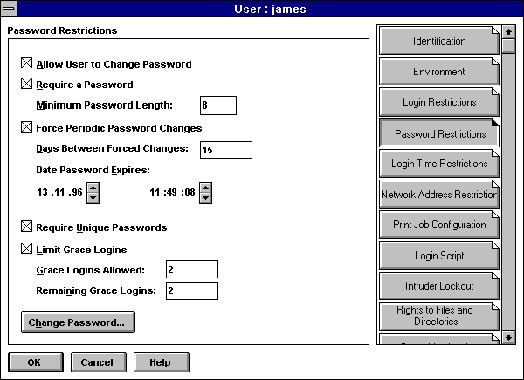
Figure 2 - password rules
Login restrictions
I mentioned above that computer access security also could be limitations as to when the user has access to the system. Users can be denied logon at certain times, for example outside the working hours. This lessens the possibility for intrusion. Other possible restrictions can be:
- Limitations in the number of parallel logons. This way lets a user know if there is somebody in his home-area. The downside is that it is often practical to be able to access several workstations at the same time.
- Limitations as to which workstations a user is allowed to use. He can, for example, only log on to his own workstation. This negates the advantage of storing files on a central server to be independent of any workstation.
- Limitations as to when a logon is allowed. If a firm has a very high security level, it might be useful to limit the logon period to working hours any weekday, and not in the evenings and weekends. This closes the network in those periods of time when the network is at its most vulnerable. If this is used in combination with a limitation to the number of simultaneous logins (max. one) the user can be almost completely sure there is none using his account while he is using it.
Again we will take a look at Novell as an example, and we can list the following login restrictions:
- Account expiration date - after this date the account is disabled
- Time limits - limit possible logons to certain times of the day.
- Limit logons to certain workstations.
- Limit the number of errors while entering a password before an account is closed.
One of the most important security measures is to make sure you are logged out of the network when your workstation is not being used. You should never leave your workstation "open" if there are material on it that not are meant for unauthorised users (and that should be the basis of this lesson). Some methods against "low-memory" users are:
- Automatic logout after a timeout period. Open documents are saved automatically and the user is logged off. The user has to run the full process of logging on and opening everything to become operational again.
- The workstation is frozen in its current condition (Locking) after a timeout occurs. To open the workstation a password has to be entered. The timeout period has to be adjusted for each person. It is bothering to have to enter passwords after long thought breaks, but a long interval increases security hazards. This is also true for a)
Encryption and PGP
Communication over telephone lines or direct lines is a great security hazard. It is relatively easy to spy on these lines and read the messages going over them. Therefore sensitive information is often translated to a coded form, it is encrypted, before it is sent. This renders the information unreadable for anyone who does not have the encryption key that has to be used to be able to decode the message. An example of such information is information about patients being sent between different health institutions over the network. In Norway the "Datatilsynet" (The bureau for computer security) has strict rules for such encryption.
On the server there is a file that is a list of all the users of the network and their passwords. This file is always encrypted. This makes it impossible for anyone to read the passwords even though they are given access to the file.
An eternal problem concerning encryption is how am I supposed to give the key to my partner? Sending the key with the message is a bad idea since this negates the meaning of encrypting the message. It is also a bad idea to send the key in another message. A better idea is to bring their suitcases, and swap them discreetly so that the key is delivered, but this is a hopeless method, especially if the recipient is located far away. This shows us some of the problems with traditional encryption and key distribution (figure 3).
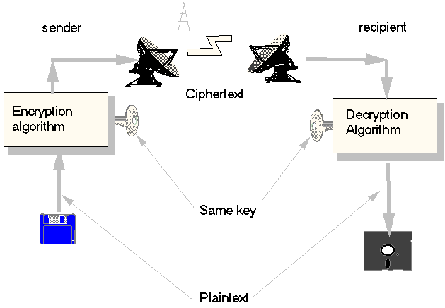
Figure 3 - Tradional encryption
Encryption algorithms are advanced technology, and I will discuss briefly one of the latest methods. Some of the first encrypted messages I encountered in my life were messages from a club called "The Mickey Mouse Club" in Norway. These secret messages were a collection of letters, for example XACVFEVHHVSGSSG, and could be read by placing a special "filter" that filtered out some letters that gave a special meaning. This is one of the simplest forms of encryption, and the key was the "filter".
The more advanced versions are developed, and they use a combination of different technologies. The method I will discuss here is the RSA-algorithm. It is named after its inventors (Rivest, Shamir and Adleman) and is patented in the USA. This algorithm (and other asymmetrical algorithms) has a pair of keys, in stead of the original one key which are delivered in a more or less secure way. Every user of this algorithm has two keys, a public key that is available for everyone (often located at a persons homepage), and a private key that is even more secret than the code for your American Express card.
How does this algorithm work, and how can I be certain that only the one I send the message can read it? Before I send a message to a person, I encrypt it with the public key of this person, it is probably located on the persons homepage. The only way to decode decrypt the message is to use the person's private key. We can see that there is a connection between the public and private keys. It is only possible to decrypt an encrypted message with the private key. This connection is very complicated, and nearly "impossible" to discover. Figure 4 shows you encryption with the RSA-method.
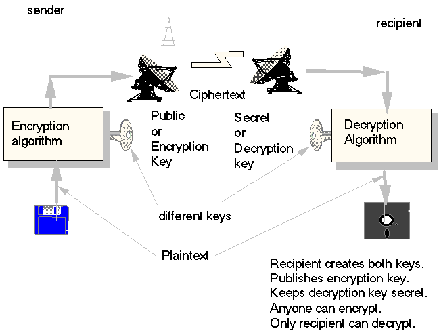
Figure 4 - Encryption with pairs of keys
The scenario outlined above is called confidentiality assurance and discusses the theme that the sender should be assured that only the recipient is able to read the message. Another well known problem (or challenge) is authenticity assurance - how can I be certain that the sender actually is who he claims to be? To control authentication a message encrypted with the senders private key is sent. To read this message it has to be decrypted with the public key. If this gives a readable message, the receiver can be sure that the sender is who he claims to be, since the keys only exists in pairs, and only the keys within a pair can decrypt each others messages and come out with a readable message.
How does the encryption work? The problem with the RSA-algorithm is that it becomes increasingly more difficult as the length of the message increases. Symmetrical algorithms (for example the DES-algorithm) are linear. Asymmetrical algorithms do not increase proportional with the length of the text, but exponential (figure 5).
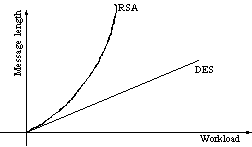
Figure 5 - Calculation complexity
This is where the PGP (Pretty Good Privacy) is good. This system has considered that messages often are long, and that it is not practical to use RSA on the entire message. PGP uses the DES algorithm, which is a more than good enough algorithm, for encrypting the message, while the key to the encrypted message is encrypted using the RSA-algorithm (this is pretty heavy stuff, but just hang on ). Now we have conquered both the problem with key distribution and the RSA complexity. Figure 6 shows such an encryption. We can see that the message is encrypted with a traditional algorithm (DES). It is important to choose a key large enough to ensure secure transmission. The key to the DES -algorithm is not sent with the message, but is encrypted with a secure method, namely the RSA-algorithm Now the encrypted key can be sent together with the message.
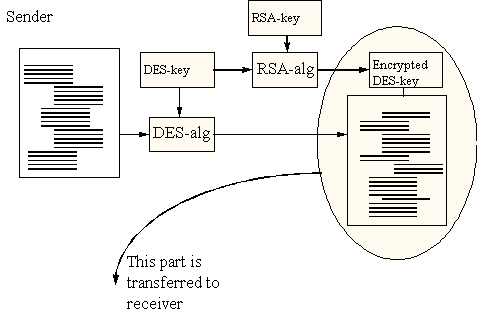
Figure 6 - PGP-encryption, sender
At the receiving end the key has to be decrypted first (using the RSA-algorithm). Next the message can be decrypted using the freshly decrypted key (figure 7).
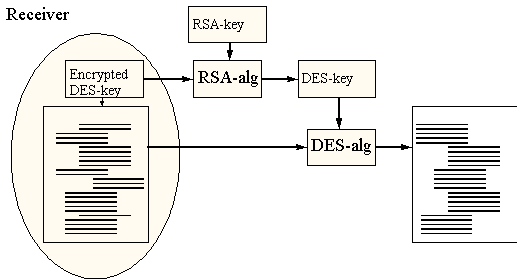
Figure 7 - PGP-decryption, receiver
A problem with such encryption algorithms is that there is always some one you must trust, a Trusted Third Part (TTP). The threshold for what is considered good security is often set high when we talk about computer security. There has to be trust in those who distributes keys to have faith in the method. There also has to be trust in the partner not to pass his private keys on to others. The meaning of RSA and PGP is that there should be as low risk as possible that there are any unauthorised people who are able to intercept and read the messages, and this is one of the best methods today. A good users guide for PGP is located at http://www.cnet.com/Content/Features/Howto/Privacy/index.html. The short article located at http://raphael.math.uic.edu/~jeremy/crypt/contrib/kurzeja2.html discusses key distribution concerning PGP.
Novell NetWare and security
In the introduction we mentioned something about setting up user environment, and administrating it. I will discuss Novell NetWare's security system in the end of this lesson, for both files and objects. I introduced Novell NetWare as an operating system, and especially NDS; in an earlier lesson.
Concerning security, Novell and others has made it to a principal that users only get access to what they need, but not more. It would be an immense security hazard if everybody were to have access to everything in the network. There has to be areas that are private, limited, and public.
Novell's file security
Novell uses the term trustee about an object (for simplicity's sake we will only look upon user-objects as trustees in this lesson, but we could be looking at all objects as trustees). A trustee is a user who has been granted certain rights concerning another object. In Novell different trustees are granted different rights:
| Supervisor (S) | All rights to all files. I a user has the S-right he will automatically gain all other rights. |
| Read (R) | The right to read or open a file. |
| Write (W) | The right to write to a file |
| Create (C) | The right to create a new file |
| Erase (E) | The right to delete a file |
| File scan (F) | The right to scan a folder and it sub folders to create a list of files. It is similar to the DOS commando DIR. |
| Modify | The right to change file attributes (a level of security we will not discuss here). |
| Access Control (A) | The right to grant rights to files and folders, not including the S-right |
Please mark that there are small differences between file-rights and folder-rights. The eight types of rights listed above exist in both cases. The difference is that the file-rights is inside the folder-rights. This means that if you have a right to a folder, you basically have the same right to the files within the folder, but not the other way around.
Inheriting rights
It was mentioned above that a right given to a folder normally also is given to the files within the folder. This is because rights are inherited from the parent folder. The same applies to the sub folders. If a user is granted a right to a folder, he is granted this right through the entire file-tree growing from that folder. This had been impossible if it had to be like this, but it does not.
The inheritance of rights can be blocked through an Inheritance Rights Filter (IRF) which is a central term in the Novell security system. This filter defines maximum rights that are allowed to be inherited to sub folders or files. If the inheritance filter is set to S and R, only those two rights will be inherited if they where given to the user for the folder above.
This filters default is set to no limitations. This means that the inherited rights are the same as those for the parent folder.
Effective rights
NetWare operates with the term effective rights for the rights a user has to a file or folder. File rights works in such a way that they are given through different ways (for example through direct grant or through inheritance). This is best illustrated with an example. Figure 8 demonstrates an example file-system.
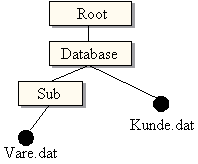
Figure 8 - NetWare rights
Imagine the user Per. He is a user in an imaginary network that has the file-structure as the one above. Per is granted the rights RWMF to the folder Database. The Inheritance Rights Filter for the folder Sub is SRF. This means that the only rights to be passed on through Sub are SRF. The effective rights that Per is granted to the file Vare.dat is therefore RF.
Please mark that the S right cannot be masked away. This is done because the system operator should not be denied access to anything, which prevents loosing access to part of the network (imagine what would happened if a user could deny a system operator access to folders. What would happen if this user forgot his password? That part of the disk would be rendered useless).
Another important feature of effective rights is the rights given to a group. The rights that are granted a group, will automatically be granted all the members. If Per in our previous example in addition was a member of a group called accounting, and this group where granted the WC rights to the file Vare.dat, these rights would be granted Per as well. Per's effective rights to the file would then be RWCF.
Novell NDS-security
Novell NetWare 4 operates with three layers of security (figure 9). To access the rights in the network, the user has to pass through all three layers.
The first layer is the login password check. We have discussed parts of this in the chapter "3.2.2 Computer Access security". There can be rules limiting the passwords, the number of incorrect attempts of logging on, or which at which times logon is allowed.
The second layer is the NDS-security. We will discuss this now. To access anything anywhere in the network, the user has to have access to objects in the NDS-tree. This access is controlled by the NDS security.
The last layer of security is the file security. This layer controls the access at the file-level and I have just discussed parts of this layer.
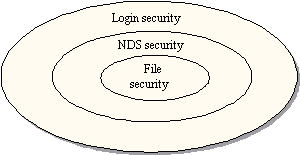
Figure 9 - Three layers of security
The NDS-security level can be divide into two parts, object-rights and property-rights. The two types of rights will only briefly be discussed here.
Object rights
The object rights are used in Novell to control the access to the NDS-structure. This means rights to read or change the NDS-tree. Examples of object rights are; the rights to view an object in the tree (everybody should not be able to see the all the objects), the right to create new objects within a container-objects or the right to delete objects.
The object rights that are available in Novell 4 is:
| Supervisor (S) | The supervisor right does still contain all the other rights. The S-object-right also contains all the property rights. |
| Browse (B) | The right to view an object in the tree. We can compare this right with the right "file scan" in the file security. This right has to be granted the container object if any object within should be visible. Normally everybody is given the B right to all objects as default when installing the network. If this is unwanted it has to be removed manually. |
| Create (C) | This right only works with the container object. With this right to a container, a user is able to create new objects that are placed in the container. The B-right has to be granted as well as the C-right for a user to be able to do anything with a container. |
| Delete (D) | The right to remove objects. If a container shall be removed, it has to be empty. Much like the DOS commando RD. |
| Rename (R) | The right to rename an object. |
Inheriting rights.
The principal with inheritance of object-rights works in the same way as we discussed under the file-right chapter. There are an Inheritance Rights Filter connected to the NDS-objects in the same way as with files and folders (which also are NDS-objects).
Figure 11 shows us an example copied form one of Novell's administration tools, NWADMIN. There are created an container object, DLN, with the user object Arne as trustee. We can see that Arne has the object rights Supervisor, Browse, Delete and Rename (and in praxis Create as well since it has S). At the bottom of the figure we can see the Inheritance Rights Filter to this container object. There are two filters; one for object-rights and one for property-rights.
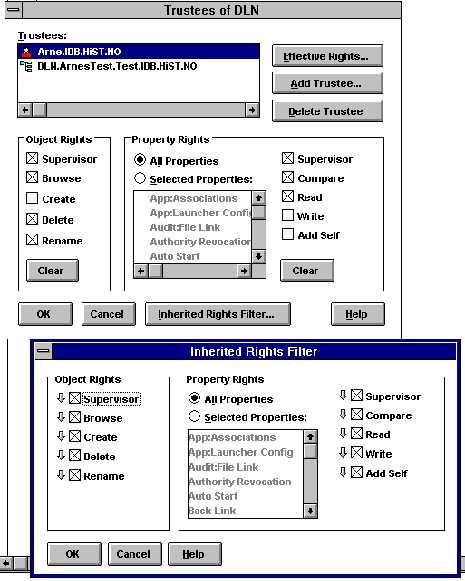
Figure 10 - Object- and property-rights
We remember from the chapter about file rights that it was not possible to lock out the System operator by masking out the S-right. However, this is possible with the object-rights. This is a bit shaky since this makes it possible to render bits of the NDS-tree without rights given to anybody. This might happened if the System-operator is masked away, and the person responsible forgets his password.
Effective rights are calculated after the same principle as earlier, as a combination of inherited rights, rights given to a user, and rights that are granted a group.
Property Rights
We saw that the object rights control the access to work with the NDS-structure. Property rights focuses one level lower, meaning that they control the object it self. All objects has many properties, a user object has properties like login-script, address information, and login restrictions. These properties is filled with values that help decide who the user is, which login-script that are supposed to run, and its password rules (as an example). The property rights controls the access to work on these.
Figure 10 shows us the property rights the user-object Arne has to the container DLN. We can also see that it is an inheritance filter connected to the property rights in the same way as under object rights.
The property- rights might be::
| Supervisor (S) | S gives a user, as usual, automatically all other rights |
| Compare (C) | The right to compare values within an object. A user can "ask" the object if the value is something or another, and a Boolean value is returned (True/False). These values cannot be viewed if this right is not granted. |
| Read (R) | The right to read the values of an object. The right C is automatically given (if you can read values, you are also able to compare them). |
| Write (W) | The rights to add, remove, or change values of properties. |
| Add/ delete self (A) | The right to add or remove yourself from the listed values, for example a group membership. |
Concerning the calculation of effective property rights, it works in the same way here as we discussed under "file-system". Normally all effective rights are inherited from the container-object above. This is limited with the Inheritance Rights Filter if it is desired. Rights given to a user or a group adds as usual.
Summary
In this lesson we have taken a look at some important principals concerning security within a local area network, and administration of this. General measures as different types of login restrictions were discussed in the beginning of the lesson. Most modern network operating systems support the elements discussed here, many systems have more.
Further on we discussed encryption and taken a brief look at how a modern encryption algorithm works. This was possibly on the border of the administration tasks, but with the introduction of the Internet in many minor local area networks, it might be useful to have an idea about such things.
Finally I discussed some of Novell's file security system, both for login security, NDS security and file security. I consider this part as quite technical and demanding for those of you who have not used Novell before. Novell's security systems are fun to work with because of its multitude of possibilities, but it quickly grows to consuming to attempt to give a thorough discussion here. There would not be difficult to make one or more classes that would deal solely with this. Those of you who wish to learn more about Novell and their security systems should seek more thorough discussions, and there are written a lot of books about this. I can recommend these two books:
- Karanjit Siyan; CNE Training Guide, Second Edition, New Riders Publishing, ISBN 1-56205-372-8
- Tom Sheldon; Novell NetWare 4, The Complete Reference, Osborne McGraw-Hill, ISBN 0-07-881909-1