Introduction
Windows NT and Novell NetWare are among the most sold systems in the world today. NT is having a quick increase (perhaps the quickest?) for its products. This is probably because whatever Microsoft does, it tends to be noticed, and because the first problems are starting to become history. The latest versions of NT seem stable enough.
It is this that has made NT to one of the more popular and best operatingsystems in the world. They have made an operatingsystem for PC's that are stable and especially made for networking. This does not apply to MS- DOS.
Background
We shall now look a bit into PC's and Microsoft history with operatingsystems. For a few years ago MS-DOS was alone (mark that Microsoft was already in) the most usual operating system for PC's. DOS was originally designed for the computers of that time, among other things with consideration to memory capacity (up to 64K RAM). Soon it was a need for a Graphical User Interface (GUI). Ms-Windows was designed. MS-Windows works primarily as an application, although it seems like an operatingsystem for the user. Windows is in other words running on top of DOS.

Figure 1 - Windows
The first versions of Windows (1 and 2) never got much sold. They had to many bugs and were simply to unstable, therefore there wasn't developed enough applications to the Windows standard. With Windows 3.1 there came a version that where relatively stable (as stable as possible with DOS' limitations?). The sales "hit the roof" and "everyone" looked at Windows as the standard for GUI. Microsoft had made a new success.
An expansion of version 3.1, MS-Windows 3.11 (Windows for Workgroups) had some extra functions which gave networksupport. A networkadapter, cables, and some configuration gave a very simple local area network. A Windows for Workgroups-system has the ability to share folders, disks or printers with other users on the net. It also opened for the possibility to communicate between users with e-mail or "chat"-functions. What's interesting with the Windows for Workgroups concept is that this introduces a new line of thought of development in Microsoft's products - an application that is both desktop (a desktop is an interface that integrates all parts of the computer/network in one interface) and a network operatingsystem.
Windows 95 is a powerful expansion to Windows 3.11, among other things they call it a 32-bit operatingsystem. Still DOS lies under, which has it's limitations. This is treated above.
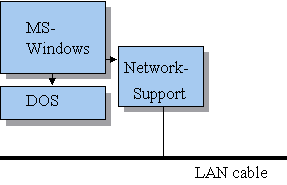
Figure 2 - Win 3.11-network
Parallel with this development goes the computer development on i.e. memory, processorspeed and disksize further on. The standard for a few years ago with memorysize up to 64K was way too small. In stead we are talking about several megabytes of memory. This brought up the need to change DOS in consideration to this. DOS was not rewritten to support the development, but it was instead made extensions to the DOS (High Memory, Extended Memory, and Virtual Memory). Another important principle that divides DOS and Windows is the way they work. DOS is not made for multiprocessing. Windows is trying to make a multiprocessing operatingsystem with the limitations it brings to have DOS beneath.
Those limitations that where mentioned earlier increases as the development still goes forward, and the stability of the Windows standard is decreasing. That is why Microsoft had to develop a new operatingsystem that should work fine for today's computers. This is where Windows NT as an operatingsystem enters. Windows NT is an operatingsystem both for workstations and for servers, or we could say an operatingsystem for networks (NOS). When it comes to administration of rights in a NT-network, there will in lecture 8 come a note about management and administration of user rights in a NT-nettwork.
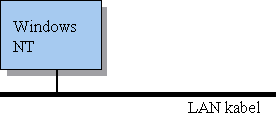
Figure 3 - Windows NT-network
NT Workstation
First we will look at a component of the NT-network, NT Workstation. NT Workstation has come to version 4.0, and has an interface much like Windows95 (Figure 4). What differ NT from other operatingsystems (especially DOS) is the high level of security and the stability of the system. NT fails more seldom than other operatingsystems/desktops. An important reason to the high security of NT is the filesystem. The filesystem tells us about the way the disk is organised. NT can be ran on two different filesystems:
- FAT-filesystem (File Allocation Table) which is the same as the one used in dos. This is not a very secure filesystem. We will return to this later in the lecture.
- NTFS (NT File System) is made for the NT operatingsystem, and is so safe that it is impossible to get those data that are locked.
Figure 4 - NT Workstation interface
Organizing and users
The biggest difference you discover between traditional Windows-systems and NT is that it is operating with users in NT. The principle is that it is defined a users who are allowed to use the workstation. It is impossible to enter a system without authenticating as a user with a password. There can be defined as many users you wish, and each one could get rights to their areas on the disk. It will be completely impossible to get data you do not have access to. This is only valid when we use the NTFS file system. FAT is not designed to be able to do this, and it is therefore possible for everyone to read everything on the disk by going outside the NT. The simplest way to do this is to boot the computer with a DOS boot disk, and then get access to all data. This is impossible with NT. But it also means that it is difficult to reach your own data if something unpredicted should happened to your own computer. An example based on my own experience shows this.
I once got an disk error on my NT Workstation. The damaged part was the one who held a part of the NT operating system (The logon part). It did it impossible for me to authenticate, and I lost all access to all data, even though they actually were intact on the disk.
The way I solved this, was to connect my harddisk as a slave-disk at somebody else's NT Workstation. Then the authentication was done through another computer running a NTFS system, and this gave me access to all the data since I didn't have to read the damaged area.
At installation of a new NT-system there is made three users:
- Administrator - this user is the one who will manage the workstation, and does therefore have access to all files and services on the computer. Usually this is the user who will be used to administer sensitive files where it is critical if anything is deleted or changed without control. Usually the normal user is not given the password for the Administrator.
- Personal user - this user is the one that is the normal user who will use the workstation. Usually this user is given access to folders containing information or other normal files, while it is given restricted access to system files and other files concerning the operating system and settings. This is of course dependent on the user competence.
- Guest - this user is for those who are allowed access to the workstation, but who do not usually use it. It could, for example, be practical if a colleague is in an office, and need to do a simple network operation (for example printout from a rapport from the network). The guest user can be sat up in a way that gives almost no access to the computer, but access to common resources on the network.
It is possible to make as many users you want to, and give access to different files or resources as it is needed. The tool used to do make or administer these users is User Manager. Figure 5 shows the main menu within User Manager. A closer look at user administration and rights will come in an later lecture.
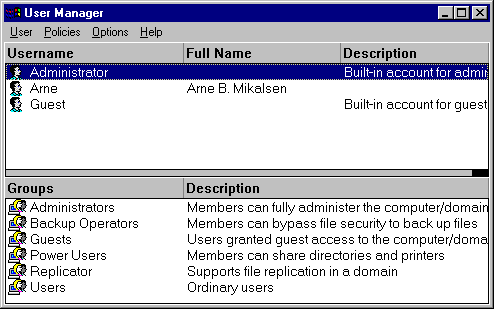
Figure 5 - User Manager
Groups
We can see from Figure 5 that one of the fields in User Manager is "Groups". This is also an important concept in administrating NT workstation. Figure 6 shows us who is a part of the group administrators at mine NT Workstation. The user Administrator is a natural part of this group. In addition I have placed my own user in this group. This gives me the same rights as the Administrator on my own workstation. This is only recommended for user who know the NT operatingsystem well. The other groups are:
- Backup Operators
The members of this group has the rights to backup the workstation. Often the users of a workstation don't have the right competence to make a backup. That is why you can use a backup operator for this task. Members of this group can also, of course, copy files back if there has been a failure. - Guests
The users of this group has guest access to the computer. The only right the users of this group have is to log on. They then get access to a very limited area. - Power Users
Users in this group have access to the computer through the network. Then they have the possibility to access files on the computer, or they can shut it down. - Replicators
A special service/group that will not be discussed any further here. - Users
This group is for all the normal users on the system. In the principle this group is the same as the guest group, but it is normally set up with more rights. The rights of the users in this group can be different, among other things the rights to which files are folders they are able to read.
Its fully possible to be a member of several groups at the same time. The "owner" can easily be a part of "Administrators", "Power user", and "Users". Then this user has rights to do almost anything from anywhere on the network.
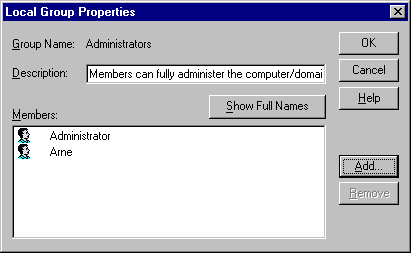
Figure 6 - Administrators
The Administrator
In older systems (for example DOS-systems) there was no difference between administrators and normal users. There are no users at all on dos-computers. Why this sudden need for administrators? The answer is actually that users on a PC actually are users. A normal user wishes to be able to use the computer as a tool to write text, make spreadsheets, copy files and so on. Normal users do not care about how the network is organised, how the operating system are set up or where it is localised. Specially hired people who work with professional computer systems, the computer-service branch, do these tasks. Bringing administrators to the PC is done to make it almost impossible to do anything wrong on your own workstation.
The administrator's tasks can, among other things, be the following:
- Install NT and make it operational
- Install and upgrade software on the computer
- Install and upgrade hardware (new adapters, printers, etc…)
- Make backups
- Keep the local part of the network structure up to date.
- Implement and configure e-mail-system
- Secure data within the system
This is a few of the tasks for the PC's Administrator. The last task is definitely the most important. The more people using the workstation, the more important the task is. It is a big and serious security problem that all the people having access to the computer can fin all the information that is located on there. This is eliminated with NT Workstation if it is secured properly
Administrator has software integrated in the NT to help with the administration of the security. Some of these are:
- User Manager - discussed earlier
- Print Manager - Makes it possible to connect printers locally or through the network, and to assign users in a way that makes it usable to only those who are authorised to use it.
- File Manager/ Explorer - used to give different users different rights. This tool is, for example, used to make "home-areas" to the users, and to assign rights so that only the assigned user can use it.
- Disk Administrator - Makes is possible to add more disks, or to make partitions on a disk.
- Tape Backup Program - Makes it possible to backup the harddisk to tape, and later on restore the data to the disk after an eventual disk crash.
Password administration:
Users accessing a NT Workstation has to enter a password to access their user. The passwords are one of the central, and wounerable, points in a security system. If it is used a bad password which is easy to discover, there is little point in any of the rest of the security system. It is possible for the users to change their password (if the administrator allows the users to change their passwords.) Clicking the button marked "Change Password" lets the user change the password. It is also possible to set an password strategy by setting any combination of these four choices:
- The maximum age of a password. This decides how often the users have to change their passwords. When the maximum age of a password is reached, a dialogue-window opens and instructs the user how to change the password.
- The minimum age of the password. This decides how often the user can change their password.
- The lowest possible length of a password. This decides how many alphanumeric digits the password, at least has to be. The longer a password is, the higher the security is.
- Unique password. This decides if the system is to remember old passwords. If the users is not allowed to reuse passwords, it is possible to set the number of passwords the system is to remember, and to compare new passwords against.
Types of NT-systems
As mentioned in the introduction to this lesson, NT is an operating system both for networks and for workstations. This is an important difference from Novel NetWare, which is an operating system for networks only. It is possible to use a Windows NT Workstation as a workstation in a Novell network. The only thing you have to do is to use built in network clients in NT, or to fetch an external client from Novell NetWare which makes the connection between NT Workstation and Novell server. In this lesson we will concentrate on NT only, and therefor we will not discuss this configuration further. We will in this lesson discuss various types of Windows NT-systems from stand-alone-workstations to the more advanced networks with NT server.
NT Workstation as a stand-alone-computer
This alternative we have been discussing in the previous chapter. The advantage with this system is that several users can share one computer, and also have their own areas on the disk. Another advantage is that it is difficult to damage anything in your own computer if the system is set up properly..
Peer-to-peer networks
We have in an earlier lesson studied peer-to-peer networks. That is a network connected in a way that makes none of the computers a dedicated server. The workstations are in stead connected in a way that makes them able to share files and resources. Windows for Workgroups and Novell NetWare Lite are examples of such systems. NT Workstation runs a very advanced operating system, and is able to be a part of a peer-to-peer network. We have seen that it is possible to connect several computers together using network adapters and cables, that it is possible to share files and resources and that powerusers, which can use remote logon, can be defined. This works well enough if there isn't too many workstations and users. When the number of users and workstations increases, such a network gets difficult to supervise.
Full-scale networks
First face in updating an business' computer could be to buy NT Workstation and connect them in a fashion like the one discussed above. Sooner or later it often rises a need to have a dedicated computer handling the network, and running server software for the other computers. E-mail is a typical example of such a program. That brings a full-scale network in as a natural alternative. Such a network uses one or several computers as servers. We will be discussing such a configuration during the rest of the lesson. But first we have to discuss an important of the NT-terminology, the domain-structure.
Domain-controlled networks
One explanation of domains could start in a network where the number of users has grown so much, that it has became a to big to administrate properly. We have seen that it is possible to set up a peer-to-peer network in a way that allows sharing of files and resources. Defining every user to a workstation does this. When an external user wants access to anything on a workstation, the username and password is sent encrypted over the network. These are checked (the user is authenticated), and the user is granted access if the user is registered, and the password correct. When the network grows, a change in the user configuration or passwords has to be updated in every workstation in the network. This tells us that there is a limit to the number of nodes in a peer-to-peer network.
This is where NT defines domain-controlled networks. In such a configuration one of the computers are set to be a server, and then also a domain-controller. The domain-controller has the responsibility to keep a list (a domain-list) over all the users in the system. Then all the user configurations can be located on the server in stead of on all the workstations on the network. When a Workstations boots, it contacts the domain-list. The authentication of users on their own computer, or for other users, is done through the domain-list instead of locally. Telling the computer that there is a domain-controller configures this. Figure 7 shows us an example of a NT domain. Here te computer running NT Server is the domain-controller.
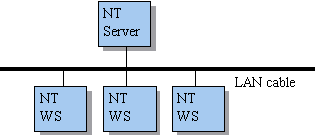
Figure 7 - NT domain
A computer has at least two advantages by joining a domain:
- The domain-controller gives information about all user accounts. Users can therefore log on to any computer within the domain. They will find their user account the same on every computer they log into (all the configurations are the same). This makes the management of the system very much simpler.
- Computers accessing the domain can be administrated or managed completely from another computer on the network. The administrator does not have to find the computer to service it.
It is possible to have different types of configuration concerning domains. It is, for example, possible to define several domains under one network, and thus keep the users to each domain separated. It is also possible to define a domain for several servers.
When workstations is configured to be members of a domain, you can choose whether you want to log using the domain-list, or if you want to use local users. It is possible to delete all local users except the administrator for use in emergencies. This forces the user to log onto the network through the domain-list. This brings an easier administration of the network.
NT Server
The NT Server is almost the same as a NT Workstation. The difference is that the Server version has some added functions to simplify the administration of the network. The most important function NT Server has is to be a domain-controller. A NT server can either be the domain-controller for the network, or it can be logged on to another server which has an domain-controller implemented. There always has to be a domain-controller, and if it is only one server, it has to be one.
There are a few additional functions on a NT Server. Some of these are login restrictions. That means restrictions as to when the users are allowed to log onto the network (from time of day to time of day) and from which workstations, which workstations are defined as workstations, and when a user account expires. All this is done from the server version of User Manager.
Other components in NT Server 4.0
The latest version of NT Server is version 4. There is much information (or bragging) under the Microsoft web site at Error! Bookmark not defined.. Bundled with NT Server there is some additional software. I will briefly discuss those here.
Internet Information Server 3 (IIS)
IIS is a Web-server that is integrated as a part of Novell server version 4. There are several advantages to using a web-server that is integrated with the rest of the network. Controlling and accessing files becomes whole concerning rights and security. IIS is described under http://wwwmicrosift.com/iis/default.asp .
Index Server
Index Server is software for, among other things, making searchable indexes over all the information on the network. More information on Index Server is located on Error! Bookmark not defined..
FrontPage
FrontPage is Microsoft's latest web publishing packet. It is made to be integrated with the rest of Microsoft's products, among other NT Server and Microsoft Office. More information on Error! Bookmark not defined..
NetShow
NetShow is what Microsoft calls a "multimedia platform" for the web-server IIS. NetShow supports among other things conferences over network, with both sound and picture. More information on Error! Bookmark not defined..
Conclusion
This lesson has given an introduction to one of the more popular network operating systems, and which probably has the most rapidly increasing interest, Windows NT. We have seen that NT s both a operating system, and desktop for workstations, and a network operating system for advanced systems with servers. We have not been discussing advanced configurations of NT-networks to deeply. That is beyond this course. What we have seen is that it is possible to design advanced systems with good implementations of security through NT's domain structure.
This lesson has , hopefully, given a good base for understanding NT, so that we in a later lesson (lesson 8) can discuss how to administer rights in a NT-network.