Introduction
In the previous lesson we discussed central topics that exists in a network operating system. Some actual types where discussed, among those Novell NetWare. Novell NetWare is fighting Microsoft NT about being the best operating system in network technology, and we might say that they are slightly in the lead?
Novell has long experience with networks, and has, in many eyes, the best competence. Many are prone to say that Novell NetWare has their strength in large network solutions, while Microsoft NT works best for smaller networks, and then mostly as application server.
Many tests confirm what is proposed above. - Novell NetWare is best when tested with large networks (over 100 nodes) with large traffic (see last lesson).
This lesson will introduce Novell NetWare and those principals important concerning this. NDS (NetWare Directory Services) are such a special topic for Novell, and important to know when we are to discuss network operating systems. We also discuss briefly how Novell set up its security system (that includes file security and data security).
This lesson is not educating experts in managing Novell-networks. The goal of this lesson is to give the students a introduction to Novell NetWare, and is to make a basic understanding for further lessons of specific problems with supervising these networks.
During the term there will come an appendix to this lesson that discusses the network operating system Windows NT on the same level as it is done in this lesson.
Summary:
Versions
In lesson 4 there where given an introduction over what versions of Novell exists. This will not be discussed further, but I will briefly repeat the most important differences:
- Network 3.* is made for large networks connecting up to several hundred users. It has good support for several platforms, such as OS/2, DOS/Win, UNIX and Macintosh. There are several that use Novell NetWare 3 in their networks at present day.
- NetWare 4.* is the last version in the Novell-family. The support for connecting several local area networks which is not physically placed close (WAN) has been updated greatly. An important new principal being introduced with NetWare 4 is NDS (NetWare Directory Services). Briefly told, NDS is a object oriented model which systematises all the resources (servers, workstations, users, files, printers, etc.) in the network. We will discuss NDS further later in the lesson. NetWare 4 is a 32 bit operating system, which makes, among other things, memory management more efficient.
System Fault Tolerance (SFT)
Novell has worked hard on the security. They have developed an security concept, and called it System Fault Tolerance. This is an formalised description if the security. It is possible to get different levels of SFT considering what need there is for security and the economy in the business. We will discuss the levels SFT can offer later in this lesson.
Generally about protocols
All communication builds upon on or another communication protocol. The widest spread protocol is TCP/IP, which is the protocol Internet uses. Novell NetWare uses a protocol called SPX/IPX. It works much in the same way as TCP/IP. Said very non-precisely, we can say that SPX is exchanged with TCP and IPX with IP. To understand this, a certain amount of understanding of layered communication protocols is, are needed. I will discuss this briefly, even though this really belongs in a class like computer communication. I feel that it is important to know a bit about what is placed under the skin.
When we work with computers that are supposed to communicate, we are depending on several things. Manly there has to be a physical connection between the computers, a net. This can be a local area network (LAN), a connection of independent computers (for example with modems) or it can be a connection of many local area networks and computers.
Secondly there has to be a protocol A protocol is a compilation of rules for how the computers are supposed to communicate. All communication over Internet is using the same protocol, TCP/IP (Transport Control Protocol/Internet Protocol). We will return to this protocol later in this lesson.
One of the problems in the computer world is that different networks talk different languages (or protocols). There has been made several translators who can translate these codes to other standards, but the basic problem that there is many protocols will still exist.
When we talk on the Internet (or generally through TCP/IP-networks), messages from one computer to another will usually pass through several networks to reach the receiver. This message is divided into small packages, which are addressed. The packages are the released on the net, and each package has to find it's way to the receiver, which hopefully also is the fastest one.
If we elevate one level up in the computer communication model, we will find the application layer. It is not enough for the computers to be able to communicate, if the users cannot exchange data through applications. Basically it is not possible for an application (for example an e-mail application) to communicate with another. We also has to have applications who talk the same "language" or uses the same communication standards. There does exist many applications who builds bridges to o applications using other standards (for example Word and WP) making them able to communicate to a certain degree. This problem can be illustrated by an simple example:
Two drivers collide somewhere in Italy. They talk different languages (Norwegian and Italian). Both are talking and gesticulating, but none of them understand each other. If each of these (coincidentally) had brought an Indian friend along, the Indians could translate by using Urdu as a bridge for understanding. This way the Norwegian and the Italian is talking with each other.
This layering can be illustrated with figure 1. We imagine an e-mail application that has an interface to the user, using buttons for "send" and "read" that are connected to an Internet address. This is a language the user easily understands. It is, off course not possible for the network (the cables) to send such signals. Down on that layer there are only sent electrical signals. The e-mail application is therefore running on top of a network application who are able to translate messages using the correct protocol being used on the network. The network application runs on top of a network driver who send the signals out through a network adapter which passes the signals on to the cable. On the other side the signals will pass on from the cable to the adapter, further up to the driver, and up to the network application that translates the signals to a message, that is read by the e-mail application.
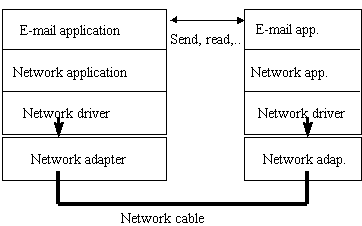
Figure 1 - Layering
TCP/IP
TCP/IP is an abbreviation for Transmission Control Protocol / Internet Protocol, and as the name says, this is a standard or a set of rules for communicating over internetworks. Internetworks are an collection of networks, and Internet is an example of this. TCP/IP is a big protocol, and id designed with consideration to the big variation of networks and hardware. TCP/IP specifies a method for addressing computers on the Internet, how data packages are routed from one network to another and how data are delivered to a process/application that runs on the receiving computer. We will not discuss TCP/IP any further here. If you would like more information, there are some references in the end of the lesson.
IP - Internet Protocol
We have seen that it is impossible to communicate if different languages are used. IP is the communications protocol that TCP/IP-networks are based upon. This protocol specifies in detail how the computer communicates, how the data packet is to be stored and how a router decides routes in the net. All computers connected to a TCP/IP-network has to use the rules of the IP-protocol.
If a computer is to communicate in IP-format, it has to run IP-software. This is because a computer doesn't understand the IP-format directly. This means that the base software for a TCP/IP-network is the IP-software. This is necessary for the presence of communication
Addressing in TCP/IP was mentioned above. The IP-standard defines a way to address. This addressing is done with a IP-number. The IP-number consists of a numberseries using a length of 32 bits. An example of an IP-number is 158.38.61.132. This addressing is administered by a the name-service DNS (Domain Name System). Each local area network in the administration network is given a number-series and defines a subnet. Such a subnet usually consists of 254 possible addresses, but it is possible to increase the number of addresses if it is necessary. The division of IP-numbers is to much to discuss here.
TCP - Transmission Control Protocol
TCP is a description of the other part of TCP/IP. In the section about IP, reliability and guaranties for the arrival of IP-packages was not mentioned. It was mentioned the data that is to be transferred is divided into packages, but we did not say anything about the administration of these packages (The splitting into packages, and splicing of several packages to whole data). For example we said that each packet is sent independently. This makes it possible for packets to arrive in a different order. Somewhere something has to sort the packages, so that they can be read in the same order as they where sent. All these tasks is done by the TCP layer.
TCP arranges error free transfers. This means that there is a error control built into the protocol that guaranties error free transmission of IP-packages. This means that a TCP/IP-network is error free. We can summarise the solutions to the following problems that are solved in the TCP-layer:
- A router is sent to many IP-packages and has to "loose" them. TCP detects this and notifies the sender for a retransmission.
- It was mentioned that the packages can use different routes through the network. This makes it possible for the packages to use different times on the transfer, and therefore arrive in a different order. This is solved in the TCP-layer since the packages is numbered, and the TCP has the responsibility to set the packages in their right order.
- If duplicate packages arrives (A router can, for example, send a packet twice) TCP will only accept the first version of the package as a part of the transmission.
TCP/IP-layering
In the section above we have seen that TCP/IP is a layered model (also called the TCP/IP-stack). This layering is shown in figure 2.
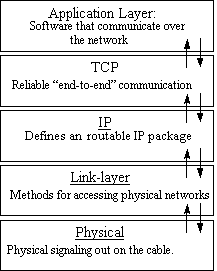
Figure 1 - The TCP/IP-stack
Wide support
Because TCP/IP is the standard used for the Internet, there is a wide support for many applications. There produced much software for the software-layer now, and many of the applications that are made is freeware or shareware.
A part of the application-layer in TCP/IP is the protocol SNMP (Simple
Network Management Protocol). As the name say, SNMP is a protocol for network
administration. SNMP can give nodes a status, such as if a Workstation is turned
on, and if they are active or free. SNMP also keeps an eye on other network
components (for example printers). SNMP is able to detect problems in the
network, and then notify an administrator about them. There is many other
functions in SNMP, but that will not be discussed in this lesson. SNMP gives
TCP/IP support for many different administration tools (for example remote
administration).
SPX/IPX
NetWare SPX/IPX (Sequenced Packet eXchange/Internetwork Packet eXchange) is the protocol Novell NetWare uses as communication protocol. The layering in this protocol is similar the one we discussed for TCP/IP. The TCP-layer is exchanged with SPX, and the IP-layer with IPX, other than that, the architecture is the same. The basic technical details discussed under TCP/IP (error free transfer, dividing into packets, etc) will also go for SPX/IPX.
Novell's filesystem and security
NDS NetWare Directory Services
We mentioned in the introduction that NDS is the most important change from Novell 3 to Novell 4. The meaning with NDS is, according to Novell, that the operating system shall be network oriented and not server oriented. Traditionally a network has been server oriented. That means that if a printer should be installed, it had to be connected to a server. If the printer is moved, all the drivers and connections to the server has to be removed, and the printer has to be installed on a new server, even if we still are on the same network. Ideally a server should enhance the efficiency of the network, it serve the network, and this is what NDS supports. We are therefore going to give a short introduction to NDS so that NDS and its advantages is known. It is not possible to discuss NDS in full here. There are a lot of literature about NDS.
In a NDS network there is only one logical network, even though there is many servers connected. This means that if we install a printer in the network, it is in the network even though it may be moved or even removed.
NDS also has a good possibility for distributed management of the network. In earlier versions of Novell the network had to be administered from the server. Now the administration-software can be started an ran from any workstation. The only demand is that the user has the necessary rights to do this.
We can see that understanding NDS is fundamental for understanding Novell 4 since NDS is a central component in the system.
What is NDS?
We have now discussed some of NDS's uses, but I still haven't written anything about what NDS is. NDS is a disturbed database that looks after all the resources (user accounts, files, printers,...) and services (for example printer queues) in the network.
It is easy to understand that it is a database. It is supposed to have some control over the existence of all the components in the network, in other words have knowledge about the entire network.
The database is distributed. By that we mean that it is not placed on one computer, but are spread over the entire network. This is mainly done to increase efficiency. Networks does often spread over large areas. There can be many parts or segments. If the database should be placed on one computer only, there would be a lot of net-traffic. That would decrease the efficiency of the network. When we in stead spreads the database, it can, by sensible placing the parts, decrease the traffic, and all parts would be equally used. Additionally NDS is, by security reasons, stored in "hidden" areas.
NDS is available for everyone from everywhere. All users has access to NDS and the information placed there. This means that NDS easily can be used as a telephone register over all the users.
NDS is object oriented and hierarchic. I will discuss the object orientation later. The hierarchic part means that there is several levels of the database. NDS is organised in a tree structure. As an example I can show you how NDS is organised at IDB:
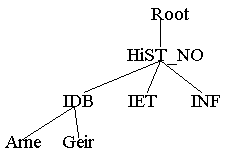
Figure 2 - NDS-example
Here we can see four levels: A root level, an organisation level (HiST), a sub-organisation level and user level. This is not the official names on the levels.
Advantages with NDS
There are many advantages with NDS. NDS can give logical names to Physical units. There is no need too call the printer LPT6 or HPLaserjet IIIp. We can just as well call it WarehouseLaser. This will often be more purposeful.
Furthermore logical organising is independent of the physical structure on the network. For most it is irrelevant if this WarehouseLaser is mounted in segment 6. It would be easier if the user could find the Warehouse by going through an organisation structure as in the one above and then localise the Warehouse.
A third advantage with NDS is that there exists one database for everything. All resources and services is collected into "one happy family". There is no longer any need for one list of users, another over printers and a third over the disksystem.
And a fourth advantage is that all resources is treated equally. The standardised interface makes it a bit more easy to enter the network operating system.
NDS-objects
All resources in NDS is called objects. An object can be a user account, a volume, a server, a printer or something entirely different. The object contains information about what it represents (for example the user account). A user account will have information about what the login name is, the users full name, his title, phone number, faxnumber and so on. The fields the user account contains (username and so on) is called the objects attributes while the values a specified object gets is called its values. An example of a part of the NDS user object arne is given in figure 3. We can see that some if the fields are empty. That is because some are mandatory, while others are voluntarily.
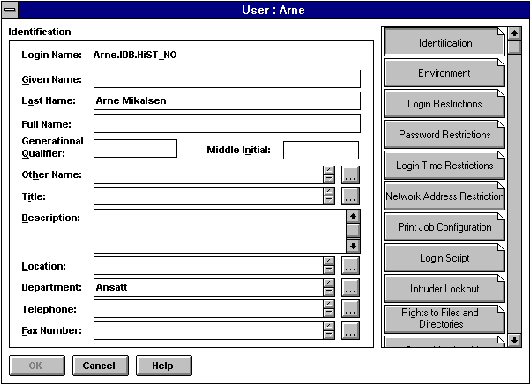
Figure 3 - NDS Userobject
Object types
It is mainly two main types of objects that can exist. This is container objects and leaf objects.
Container Objects
The definition of a container object is that it contains other objects (container or leaf objects). An example of this is given in figure 2. Container objects gives logical grouping, and it is possible to divide after a organisational structure like in the example.
Another possibility is that it opens for easy management. If a large group is to have special rights, it is possible to give these rights to the container objects. It will, for example, be possible to make two new container objects called "employees" and "students" (Figure 4). Now it will be possible to give all the employees access to a printer (or files) by only giving the rights to the containerobject.
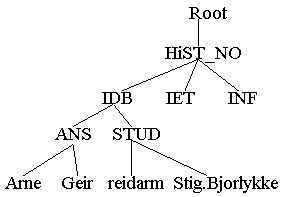
Figure 4 - NDS
There are four possible container objects:
- The root object (root) which has to be placed alone on the top of the tree (it is somewhat lice an inverted tree with the root on top...)
- The country object
- Organisation object. This object represents the organisation level in the tree (HiST). There can only be one level with organisation.
- Organisational Unit (OU-unit). This object represents departments in the tree, and it is possible to have as many departments as you wish.
Leaf Objects
The definition of leaf objects are relatively simple. A leaf object is an object which cannot hold other objects. That is why it is named leaf.
Leaf objects always exist within an container object.
Novell file system and security
Volumes and catalogues
A volume is a part of Novell disksystem. The parallel in DOS is that it is possible to split a disk into several drives (F: G: H: ). A volume is an object in NDS (figure %5).
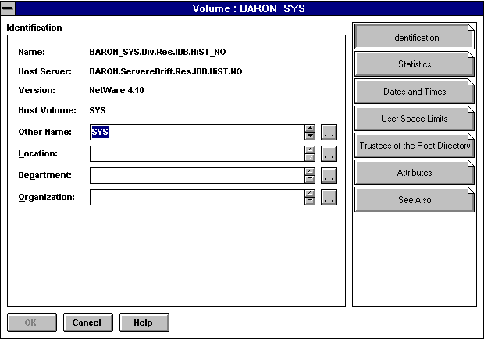
Figure 5 - Volume
It is possible to have up to 64 volumes on a NetWare fileserver. The first volume is always called the SYS-volume. This volume contains the system files Novell needs to work as an operating system.:
- SYS:SYSTEM
- Commandos and files to be used by the network operator.
- SYS:PUBLIC
- files available for everybody
- SYS:LOGIN
- files needed for login on - this part is available without any user logged on.
- SYS:MAIL
- this is mainly an antediluvian from earlier versions, and is mostly used for backward compatibility with earlier mailsystem.
In Novell terminology we say that a volume is mounted. This means that it is made available or is mounted. This is done in the start-up file AUTOEXEC.NCF which is a file that starts up when the server is started. This file can be compared to DOS's AUTOEXEC.BAT.
It is possible to mount a Novell-volume as a drive name, for example Y: with
the MAP command. The syntax for this is:
MAP Y:= SYS:PUBLIC
Novell security
In this part we are going to discuss briefly how Novell's security system works. In the lesson about management and security (lesson 8) we will return to this, and discuss more detailed how Novell defines its security.
The main thought with Novell's security is that users is only to have access to resources or files they need. If everybody is allowed access to all data, it will bring a big security risk to the entire network. That is why it has to be as restricted as possible.
Novell operates with "effective rights". This is the number of rights a user has to a specified resource. It is eight different rights a file can have:
| Right | explanation |
| Supervisory [S] | All rights- overrides all other rights |
| Read [R] | Read open file |
| Write [W] | Write to open file |
| Create [C] | Generate new file/folder |
| Erase [E] | Delete file |
| File Scan [F] | List filenames/under folders (DIR) |
| Modify [M] | Rename files/folders |
| Access Control [A] | Give rights to files/folders |
The effective rights a user has to a file or catalogue is the sum of all rights given to the user. How these rights are given will not be discussed here, but in lesson 8. It is the supervisor or one who are entitled to give such rights who can give these rights.
User security
Novell does not only operate with rights to files or folders. There is also a large security system connected to the administration of the rest of the NDS-objects. As an example of this we will discuss some of the security Novell can use with user accounts:
- Account restrictions
It is possible to set a limit to how much time and resources a user can use. It is, for example, possible to set that a user can use his account for totally 50 hours, and after those he is deactivated. Another example is that it is possible to set accessibility to office hours only.
- Expiration date
This is useful for temporary users. After this date it is no longer possible to log into that account
- Password rules
Novell can set limits as to how the passwords is constructed. A minimum length can be demanded, the presence of special signs(!"¤¤"%), how often the password has to be changed, and so on...
- Disk space limiting
- The number of simultaneous log on's.
We will return to NDS and the objects in many of the next lessons. In this phase the principals are the important ones.
System Fault Tolerance
As mentioned in the introduction, Novell sets security high in their products. System Fault Tolerance is the system that specifies general security. SFT is divided into three sublevels: SFT Level I, II and III.
SFT Level I
The following components is placed in SFT Level I:
- Verification of disk writing
- Duplication of important files, for example FAT (File Allocation Table)
- Transaction monitoring.
This is the lowest security layer (and of course the cheapest one). What happens is that when something is written to a disk, it is verificated by reading what where wrote to be sure that it was correctly saved. If any mistakes is found, they are corrected. Further more the most important data is saved in two separate places, in case one of them should fail. "Transaction monitoring" means that if a transaction crashes while transferring, SFT Level I makes sure the transaction is set to starting condition. This way, we won't risk loosing an original while the copy is only partly transferred. That is, by the way, a well known database problem.
SFT Level II
SFT Level II deals with disk doubling. The most common problem with networks is disk crashes. If everything saved to disk also is saved to a backup disk, we are protected against disk crashes. If a crash should appear, the backup disk still works. "Double" disks is divided into two main types:
- With mirrored disks, only the disks are doubled. When anything is written to a disk, it is sent to the servers diskcontroller, which writes to both disks. Most diskcontrollers support this. This variants problem is that the diskcontroller might fail.
- With duplicated disks the whole disksystem is duplicated. Even the controller. This brings us slightly higher security in our filesystem than with mirrored disks.
SFT Level III
This is Novell's highest form for security. With this variant not only the disksystem is duplicated, but the entire server. If the security is very high prioritised, each server is placed in different buildings with a high speed link between them to keep them synchronised. Now we even has protected us against fire or catastrophes concerning the other building. If the primary server should "fall down" or otherwise fail, the backup can take over control.
Login script
Login script is used to standardise settings at logon. The most usual task for the login script task is to connect to logical drive, for example Y:, to a NetWare-volume (MAP-commands). Other tasks is to set up the printer milieu as it is meant to be for each user (or more commonly; groups of users) or to give a "today's news" message.
Login-Script is an attribute (from NDS) that belongs to user accounts and Container objects.
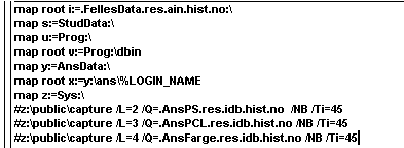
Figure 6 - loginscript
There are mainly three types and loginsscripts:
- System Login Script
- is connected to a container object (Figure 6)
- Is used by all users under this object.
- Profile Login Script
- For special configured groups of users. It can, for example, be helpful to use profile scripts for the office sportsteam members (going across normal departments and container objects) that are supposed to have a special message at logon.
- Personal Login Script
- Is made for single users and comes in addition to the ones above.
Summary
This lesson has discussed Novell NetWare. It has not been a course for systems operators in administrating Novell networks, but, hopefully, it has given an impression of some important areas within Novell-terminology.
We have also discussed computer communication protocols and looked at TCP/IP and SPX/IPX. This is mainly orientation information, but I feel that it is important to understand why things work as they do - some times anyway.
We will return to Novell and administration of Novell in several lessons later in this course - especially lesson 8,9 and 10. Novell will be used often as an example system.