Lesson: 1 - Introduction
Summary: This lesson serves as an introduction to "LAN Administration". It will attempt to set LANs in a historical perspective. In addition, it will look at the advantages and disadvantages that come with setting up a LAN.
Copyright: Arne B. Mikalsen/TISIP
What is a Local Area Network (LAN)?
Most people are familiar with stand-alone PCs. The possibilities are somewhat limited. Usually, there is just one disk from which information can be uploaded from in addition to floppy diskettes, only one person is able to use the machine at any given time and the external equipment connected to the machine can only be used by that machine. It is not until one can connect several machines together and in doing so making it feasible for these machines to "communicate" with each other that the possibilities become more plentiful. The Internet is an example of a powerful network of PCs.
Over the last few years the number of microcomputers (typically PCs) linked together by communication media into networks has increased tremendously. This interconnection within a limited area is called a Local Area Network (LAN). Reasons for setting up such a network can be numerous. One reason may be a desire to make data available to several users in a very easy manner. Another may be to share access to printers.
An important concept when speaking of LANs is resources. Resources in this context means equipment normally connected to the PC (to be taken up later), for example printers or CD-ROM drives, and data (files). What particularly characterizes a LAN is that these resources can be shared by the users of the network. A printer which may be located in a different room (or office) is accessible by other users on the network. This also applies to files. In cases where a project group works on a common set of documents, the system can be set up such that each of the group's members has access to these files. This can save a lot of time and work as the group members will not need to run around from office to office with diskettes to get the latest version of a document. Instead, the latest version can be saved on the network.

Figure 1 - A Simple LAN
In order for machines joined together by communication media to communicate in the manner described above, special software must be installed. Such software is called communications software. If we imagine a regular PC, we must have an operating system which makes it possible to download a file from a diskette or harddisk and set it in the computer's memory. In the same way, there must be an operating system which makes it possible for data to travel from one machine by the medium to another machine. This operating system is called a network operating system (NOS) and a very familiar variant of this is Novell NetWare's operating system.
Another important concept in connection with LANs is the client/server principle. We often hear about the network server. An important principle in network theory is that some resources on a given network specialize in order to perform certain tasks while others perform other tasks. We can compare this to the "real" world where some people are experts in car repair and perform these tasks most efficiently, while others are expert painters. In a LAN, resources are often set aside to service the printers. The print server will then be responsible for receiving print jobs and ensuring that these are sent out to one of several printers. When the document is done (the job is completed) the server sends a message back to the originating machine. A client (often called a workstation or PC) which requests services from a server also exists - in this case the client sends a job to print. File servers, CD-ROM servers, application servers and other types of servers operate on the same principle.
Local Area Networks and Internetworks
A network which exists within a building is a local area network (LAN) and is often constructed such that we can considered it a network. It can, for example, mean that all data packets on the net are visible to all machines or for those using e-mail and that one does not need to type in another user's entire e-mail address in order to send mail to that person. For instance, a network makes it possible to type in just the user name as an e-mail address (arne instead of arne@idb.hist.no) if they exist on the same network.
Several networks can be linked together such that "our" machine can exchange data with machines on other networks. Special machines are set up between the networks which transfer only the data which should be transferred, and which send data the "right direction" if there is more than one path and more than two networks. Networks connected in this fashion are called internetworks.
One special internetwork stretches over the entire globe and has a special form of administration. It is the Internet. This is a so-called "open" network with decentralized administrative responsibility. The Net is administered "ad hoc" whereby each participant is responsible for his or her own network. Additionally, there are few limitations/boundaries aside from a certain form of self-rule (laws and rules called Netiquette).
It is possible to connect oneself to this network and contribute to its ad hoc administration. Someone builds a "network" and buys data lines in order to connect themselves to the Internet. Afterwards they offer others the opportunity to "buy into" their network which is connected to the Internet. Those who sell this kind of connection are often called Internet providers.
Classifying Network Types
Depending upon how big a communications network is (in length and reach), three classifications of networks exist.
Local Area Network (LAN)
If the network is within a contained area, typically within a building or neighboring buildings, we can say that the network is of the type LAN (Local Area Network). Communication media usually are internal, in other words, without a permanent telephonewire connection (for example, Telenor). ISDN can be used to temporarily transfer data. The transfer rate in a LAN is usually high, preferably with several Mbps, depending upon the transfer medium.
Metropolitan Area Network (MAN)
We can tell by the name that a MAN connects units which are placed far away from each other. It is preferale to say that the distance between units in a MAN range from 5 to 50 km. That which characterizes a MAN is its speed. Even though the distance is relatively long, we can raise the speed over 100 Mbps. The transfer medium for a MAN is preferably fiber optic communication media.
Wide Area Network (WAN)
WAN use preferably permanent public lines as its transfer medium. The name itself means that the distance between components in a WAN are great. A WAN often connects several independent LANs. An example of a WAN can be a firm with several departments wishing to be connected by one network (See Figure 2).
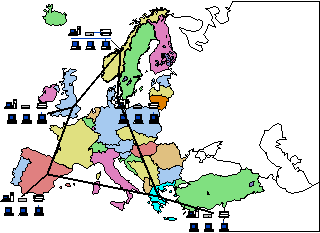
Figure 2 - Wide Area Network
Historical Development
History in connection with computer technology is a somewhat strange concept. We speak of an entirely different period than we are used to when speaking of history. The 1960's heralded the beginning of a boom in the computer's development. Then, man made computers with integrated circuits (ICs). At that time IBM's mainframe computers came into existence.
Mainframe computers
The history of the network is even shorter. In order to communicate over a network we are dependent upon communication lines, a communication medium. It was usual to use a so-called dumb terminal which was tied to a mainframe. A dumb terminal consists of a keyboard which sends out keystrokes as signals along a cable, preferably without any format at all. These signals travel to a mainframe, which can interpret the signals and, if need be, send a message back (echo) to the originating machine's screen. Such a mainframe computer would preferably be able to handle several such terminals simultaneously.
Figure 3 - MAINFRAME
A typical example of such a mainframe was Norsk Data's mainframe computer (ND-maskinene). These were used a great deal during the 1980's and were predicted a bright future. But the problem with the computer world is that the future is extremely short, and we remember ND's history as relatively short.
Microcomputers and LANs
The adaptation which ND did not make was the change from mainframes to microcomputers. The microcomputers (or PC's) became more and more powerful, and one was no longer dependent upon the computation capability that mainframe computers could offer. There continued to be a great need for the advantages provided by a network. LANs therefore became a very important concept during the 1980's. It was also IBM which launched PC's in the form we recognize them today. PC's were cheap and their computation capability had grown tremendously from the early days to now. PC's connected in a network could share resources and files, a big economic advantage (Figure 4).

Figure 4 - Local Area Network
Advantages and Disadvantages with LANs
(This chapter is partly taken from the subject "System Administration" by Geir Ove Rosvold - Spring 1996.)
Advantages of a PC-network
Resource sharing
As earlier mentioned, there are several uses for PC-networks, sharing of programs, information, etc. A common expression for this is sharing of resources. Some typical examples of how resources can be shared follow:
Printers
All the users on a network have access to printers. If one has several types of printers on the network (for example, color printers, laser printers, plotters), the system provides incredible flexibility. If the sharing of printers is the only reason for setting up a network, it may be just as wise to buy a switchbox for the printers. With such a box several PC's can be connected to the same printer.
Processing Power
In some cases it may be convenient for our PC to leave some of its job to another machine (namely a server). In this way, several machines on a network can work together on one task. This is called client/server technique. Our PC is a client which asks the server to perform a specific part of the job.
Data/files
On a network many users can have access to the same files and thereby share data which is saved there. This is a quick method to distribute information in an organization. At a school, for example, one can imagine that schedules and class rolls can be archived such that everyone can download them. Data can also be shared with the help of databases which many can be given access to.
Software
Software can be centrally located on a network so that it does not need to be installed on every single machine. In most cases, the company is required to purchase a site license which allow a predetermined number of users to utilize the software.
Disk Space Allocation
In a PC-network there is often a server with a large hard drive which everyone shares. By using a common hard drive, this allows the users to use disk space as needed, instead of each user getting a harddisk of the size 240 MB. In other words, each user can use as much or little of this centralized memory as he or she really needs.
Other Input/Output Devices
In a PC-network everyone could have access to equipment such as modems, scanners and CD-ROMs. If your organization only owned one scanner, everyone could still make use of it if it was connected to the network.
When people share resources in the manner described above, the demand for certain resources can grow so great that these become inaccessible most of the time. In such situations it may be necessary to allocated quotas to the users. Disk space is often a problem, and in many places it is such that each user is not allowed to use more than a decided amount of disk space. In some academic environments, each student is allowed to print out a limited number of pages on laser printers each year. This can often be due to economic constraints.
Communication
One of the biggest advantages of having a PC-network is that it allows for electronic communication between users -- electronic post, electronic conferences or transfer of files. Often there are additional LANs connected to a bigger network, internetwork. In such cases it may be possible to communicate with people all over the world, or to download files from a computer in, for example, Australia.
A popular expression is groupware. These are programs which can be used by an entire group of users who sit at their own PCs. This is possible because the users' PCs are connected to a network. Mail and conference are really groupware. Here are some other examples:
- A common calendar: Every user has his or her own calendar lying on the net. Whomever needs to arrange a meeting can then check everyone's calendar via the network.
- Word-processing for groups: Often there are several people working with a text. In a word processor for groups several can work on the same document simultaneously. A problem occurs, of course, if two users try to change the same setting at the same time. A system can solve this by obscuring (make a half-transparent cloud around) areas in the text where others are working.
As mentioned earlier there are relatively few who use their networks for communication purposes. A few years ago there was a lot of talk about "the paperless office" which would soon be upon us. In such an office, communication with the help of a computer network would be at the heart. However, this type of office has not come about as quickly as expected.
Central and Routine Back-ups
Making back-ups on PCs is bothersome. If it is left up to each user, it would almost never be done as a rule. (At least not before his or her disk crashes...) In a LAN where the users' files are gather on one server, a back-up copy of all the users's files could be taken at regular intervals. It would also be simple to establish routines for making back-ups. Another job for an information systems manager.
Users Can Login From Wherever
With stand-alone PCs, data is saved onto a hard disk or diskette. It is then relatively inefficient to move work from one machine to another. However, if the files are saved at a central location, one is able to login from wherever and just as easily have access to them. In some networks, it is such that each user has his or her own setup for Windows and other programs. The setup determines how the screen will look (files, icons, windows, etc.), and which standards shall be used (line spacing in the word processor, column widths for spreadsheets, etc.). This allows the user to determine his or her own setup, and it can be reconstructed regardless of which PC is used. When the user identifies him or herself with a user name (and password) this sets up access to the initiation files in which such information lies.
Security
In PC-networks one must as a rule login with a user name and password in order to receive access to files. This can be more secure than on stand-alone PCs because one does not often need a password in order to get access to the files lying on the hard drive. A central storage of data can also be less secure because many users have access to the same hard disk (see below).
Security can also be increased by keeping a log of all the activity on the system or server. By this it is meant that the machines automatically save who has done what at any given point in time. In this manner one can find out if there has been unauthorized person in the system. One can also go back to see who has done something that should not have been done.
It is worth mentioning here that such logging can only be used for security purposes. It is, for example, forbidden for an employer to measure hours worked by its employees in Norway, that is.
Less Expensive Systems
One should not ignore the big picture - it can be less expensive to invest in a network and common resources than have stand-alone PCs. The organization can then invest in "lesser" PCs with smaller storage. Files can then be saved centrally and some of the jobs can be left up to a "big" machine (the server). Survival with fewer printers may even be possible.
Disadvantages
Vulnerability
Vulnerability in a network is greater than with stand-alone PCs. If for example the central disk crashes, it affects many users. This is the same case if the server jams. Even a stop in operations for a few hours can be serious because it affects many users. Making regular back-up copies and other prevention would likely limit the damage caused by such occurrences. The manufacturers of servers are steadily emphasizing stability and accessibility. The high occurrence of downtime will therefore surely be reduced.
With computer networks it is becoming easier for viruses to spread than when PCs stood alone. In these instances good routines can also limit possible damages.
Poor passwords
Central storage of data can make it easier for unauthorized persons to access data they should not. Many examples of so-called "hackers" who have hacked their way into systems where they should not have gained access abound. The least one can do in order to protect oneself against such things is to choose passwords which are difficult to guess. In addition, it is wise to change passwords often.
Similarly, there are many stories about how a large percentage of passwords have been cracked in no time with the help of software which systematically tries words from a list. Therefore, never make passwords which are real words. As well, do not use passwords which can be connected to you. Do not use a loved one's name (neither forward nor backward), do not use car models or your license plate number, etc. Rather, you should make "strange" passwords like DLIAFWTL for example. Some systems demand that you use at least one number in the password. Then, you could choose LO2A0P. Does it seem like these two passwords are hard to remember? I will reveal the nemonic devices I used. "Distance Learning Is A Fine Way To Learn." "LO(t)2 Awarded 0 Prizes."
Costs
A string of costs comes along with having a PC-network. In large installation PCs become just a small part of the investment. What you need for a medium-large network in a company are communication media, network cards, a server (preferably a powerful machine with a lot of disk space) and network programs. In addition, it takes money to drill holes for the communication media, and thereafter lay them in all the necessary places. It will be even more costly the day you get a new employee who needs to be added to the net -- new holes and more communication media.
Installation
The costs incurred for stand-alone PCs is small. The machines must be unpacked and software loaded. On a network the installation costs can be large. This is due to:
- buying and laying communication media,
- installing network cards in all the machines,
- setting up a server,
- working with printers which are often complicated to install,
- installing network programs,
- planning and setting up users and
- training many users.
It is important to set up a detailed contract before one allows a supplier to install a network. The contract should cover what it shall do and how much it will cost. If necessary, an unbiased third party should be consulted to find out what kind of installation you have need for. The price must be agreed upon beforehand such that it becomes the supplier's problem if it uses more hours than expected. Hold back the last payment until everything works, all the users, all the printers, all the software, etc.
Maintenance
Experience shows there is also more maintenance associated with a PC-network. This is because a PC-network is a more complex system than stand-alone PCs. In a network a system manager is needed. How many hours this person must allocate to this job per week will vary proportionally with the size of the network and how often problems arise.
Training
In general, a PC-network work will require somewhat better training than if each user had his or her own PC. In a network it is important that the users learn good routines for security, and that they are conscious about where they save their files.
Performance
It is often slower to work on a network than on a local hard drive. It takes, for example, longer to open files which are saved on the server than ones saved locally on the PC's hard drive. This can have big consequences when one runs large programs (for example Windows), and these are saved on the server.
Life cycle of a Network
When a company considers installing an information system (systems development or software development) in order to simplify routines, it will be necessary to complete a project including all the phases associated with a system development project. We often talk in project organization about a life cycle model which consists of 7 phases:
- Need Analysis
- Analysis
- Design
- Realization
- Implementation
- Management
- Shutdown
The first phase looks at the firm's needs and current situation. Then it evaluates whether or not the firm's needs will really be met by installing the new system. Another phase consists of a preliminary study (evaluation of alternatives) and specifications. The creation phase tells how the demands of the specifications can be met, while the fourth phase brings these initiatives to life. After the system is implemented it needs to be maintained until it one day is shut down. This model is taken from system theory.
Concerning system development (programming) it is often a given that it will be project steered and therefore go through all these phases. Installation of a LAN has a tendency to place all of its weigh on the fourth and higher phases. This is very unfortunate. It is important to carry out a good and thorough analysis of the firm's needs and wishes. Often an investment of this size is much too large in relation to the need. Such cases can be brought to light already in phase 1 of the life cycle model.
Need Analysis
The reason behind a need analysis is to map out the firm's problems and needs. In this phase it is important to see the firm as a whole, not isolate the information system. Need analysis should end in a plan for execution and desired initiatives. If the purchase of a LAN is a desired initiative, we can move on to the next phase.
Analysis
The analysis phase consists of 2 parts, the preliminary study and specifications. In the preliminary study different alternative solutions shall be analyzed. An example of what should be analyzed are different network operating systems, electronic post systems and other applications. Hardware components should also be looked at. The preliminary study ends with a preliminary study report which shall serve as the basis for a resolution for company's decisionmakers. In the resolution one of the alternatives from the preliminary report should be chosen.
Specifications state how the chosen system shall function. It should include requirements for response time, functionality, security, training, hardware and life expectancy for the system. It should also include which parts (hardware and software) the system shall consist of.
Design
The design phase explains how the demands in the specification phase shall be met. This is a very important part of the network's documentation. Here all the drawings of hardware placement and communication media can be found. This should also include an overview over software which will be installed on all the machines.
Realization
A new network often requires some additional programming before the network can be installed. This is completed in this phase. Examples of such tasks can be adjustment to applications or script programming.
Implementation
The physical installation of the LAN takes place in this phase. Communication media is laid, software installed and computers and all other equipment placed as planned. Another important part of this phase is the training of the users together with the start up of new routines. This is a long process. Because a new network can lead to big changes in many of the employees' work situations, these changes must always be made cautiously and slowly.
Management
LANs have rather complicated operation routines because when unexpected problems pop up or if unauthorized persons access the system, the consequences can be tremendous. This is a very important task which a single person usually takes care of.
Running LANs emphasizes this phase of the network life cycle model.
Shutdown
All projects (LANs included) must at some point be shut down. The reasons are many and various, for example transition to a new system or closing of the firm. Regardless it is extremely important to carry out a planned shutdown of the network. Since so much sensitive information lies on the net, it is important to find a way to preserve the information. This can be done by filing it away by electronic/manual means or transferring the data to a new system. Simultaneously, it is important to get the information away such that it does not fall into the wrong hands. We see that also the last phase is very important in the life cycle of a network.
We can illustrate the 7 phases in a life cycle model as Figure 5

Figure 5 - Life cycle of network installation
More About this course
This course shall try to combine practical management with general, timeless guidelines. Since development in this subject area happens so fast it is important not to graduate experts in Novell 4 or NT 3.5, but rather try to provide an understanding of which areas one shall have an overview over as an information systems manager. Expertise in certain brands can be obtained from other places (for example through courses offered by distributors). Practical network operating systems (like Novell) are used as an example.
In addition, it is important to realize the fact that this is a 2 credit-hour course. Many could very well consider themselves as being completely educated after taking such a subject. But, this is not true! 2 credit-hours is the same as ca. 3 weeks full-time work, so the depth and amount of what is covered in such a course is limited.
The Lessons further on...
In the table below I have described how I imagine the course plan should look as seen before the course starts. I reserve the right to change this plan underway. As mentioned earlier, this a subject area which is developing so quickly that it may be wise to be flexible with regard to content.
| Lesson | Content |
| 1 - Introduction |
|
| 2 - Hardware Components for LANs |
|
| 3 - LAN Network Card |
|
| 4 - LAN Operating system (NOS) |
|
| 5 - Novell NetWare and Windows NT |
|
| 6 - Installation and Planning |
|
| 7 - Groupware and S.W. Protection |
|
| 8 - Operation and Security |
|
| 9 - Print Environment |
|
| 10 - Making Back-up Copies |
|
| 11 - Management Methods and Philosophies |
|
| 12 - Management of WWW-servers/Intranet |
|